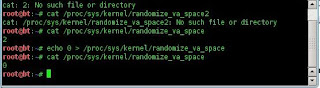
In BigAnt Server we will try the fuzzing to the "USV" command of BigAnt
server. First we run the BigAnt server then attach proses of
antserver.exe to the Ollydbg. we have restart the bigAnt server and also
Ollydbg every time we do the fuzzing.
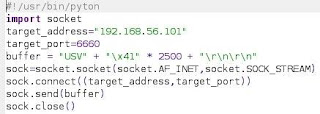
we will try to send buffer data 2500 byte to the BigAnt server. and see what will happen here
The aplication got crash but is not missing, because BigAnt server is using SEH, to see inside SEH, click view then SEH chain
it is obviously if buffer which we sent filled in SEH chain. To continue
data from SEH chain to memory, press shift+F9, and the EIP become
41414141
if we see in 3rd line from window olly dbg, buffer which we send already placed in stack. to look up the data inside of aplication memory, just right click on stack line then choose follow in dump.
Now the next steps is we need to get the "jump Stone" address .
we must to get address which is inside consist of POP, POP RETN. Thoose address will we use to overwrite SEH address in the aplication. we use menu "view" then "executable modules"
there is a two conditions of "jump stone" adress we can use to overwrite SEH adress:
a. the module is not compile using /safeSEH ON
b. The Module has not or did not use opsi flag IMAGE_DLLCHARACTERISTIC_NO_SEH
To know the location of POP, POP RETN we are using OllyDbg then "view"
then "executable modules" and double click on vbajet32.dll, after inside
of window CPU of vbajet32.dll, right click again, choose "search for"
then "sequence of commands".
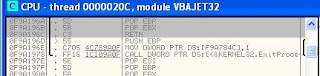
From the picture above ollyDbg found inside of vbajet32.dll address, is on offset 0F9A196A.
Get the Offset to overwrite SEH
we are using tools pattern_create on metasploit to make string_pattern for 2500 byte, then we load it into the fuzzer.
now re are running the aplication and OllyDbg again, and it has crash then we got new EIP value here
then we load the EIP value to the pattern_offset like this:
so we need around 966 byte as trigger of SEH Handler, then we use it into the fuzzer:
then we run it to the aplicatons again, then the SEH chain will be like this:
so the buffer which we loaded is true and as the planning.
Control CPU Process
To get the byte address which we use as SEH trigger now we loaded offset address of vbajet32.dll inside of fuzzer.
before we run the OllyDbg and BigAnts, we need to install breakpoints on SEH memory address, we do that just to make sure if our exploits really pointed to the target.
then press shift+F9 to pass vbajet 32dll then press F7 till reach RETN. like this picture:
because of the space memory just 4 byte and this is not enought to keep a shellcode, we need other process to relocated to the address which has enough memory space . to get it just right click on 015FFD7D then "follow in dump" then "selection". and we got like this:
Create Shellcode
same like exploits before now we need te create payload from framework mwtasploits , we will use windows reverse shell here as the picture:
after we generate the payload, we need to clear up the bad character from the shellcode , and make sure if the shell code is free from bad character with check it manually then send it row by row with fuzzer, finally the result is like this:
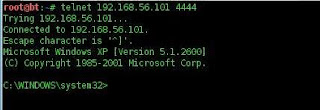
and we run it to the BigAnt server , and finally we success to remote the target: